Review of Pentester Academy - Windows Red Team Lab
You may have seen my previous reviews of Pentester Academy - Active Directory Lab which I wrote back in April after I got the certification. It is a great course intended for beginners in AD security, so if you feel like that is you, I guess you read that review first.
This is my review of Pentester Academy - Windows Red Team Lab which is the next step in their progression of Active Directory oriented certifications. This course provides an Active Directory lab that allows you to practice sophisticated attacks on Microsoft infrastructure and enterprise applications. It is harder and more complicated than the previous certification.
I actually did this certification back in May this year, but writing this review kind of drowned in other things. However, here it is!
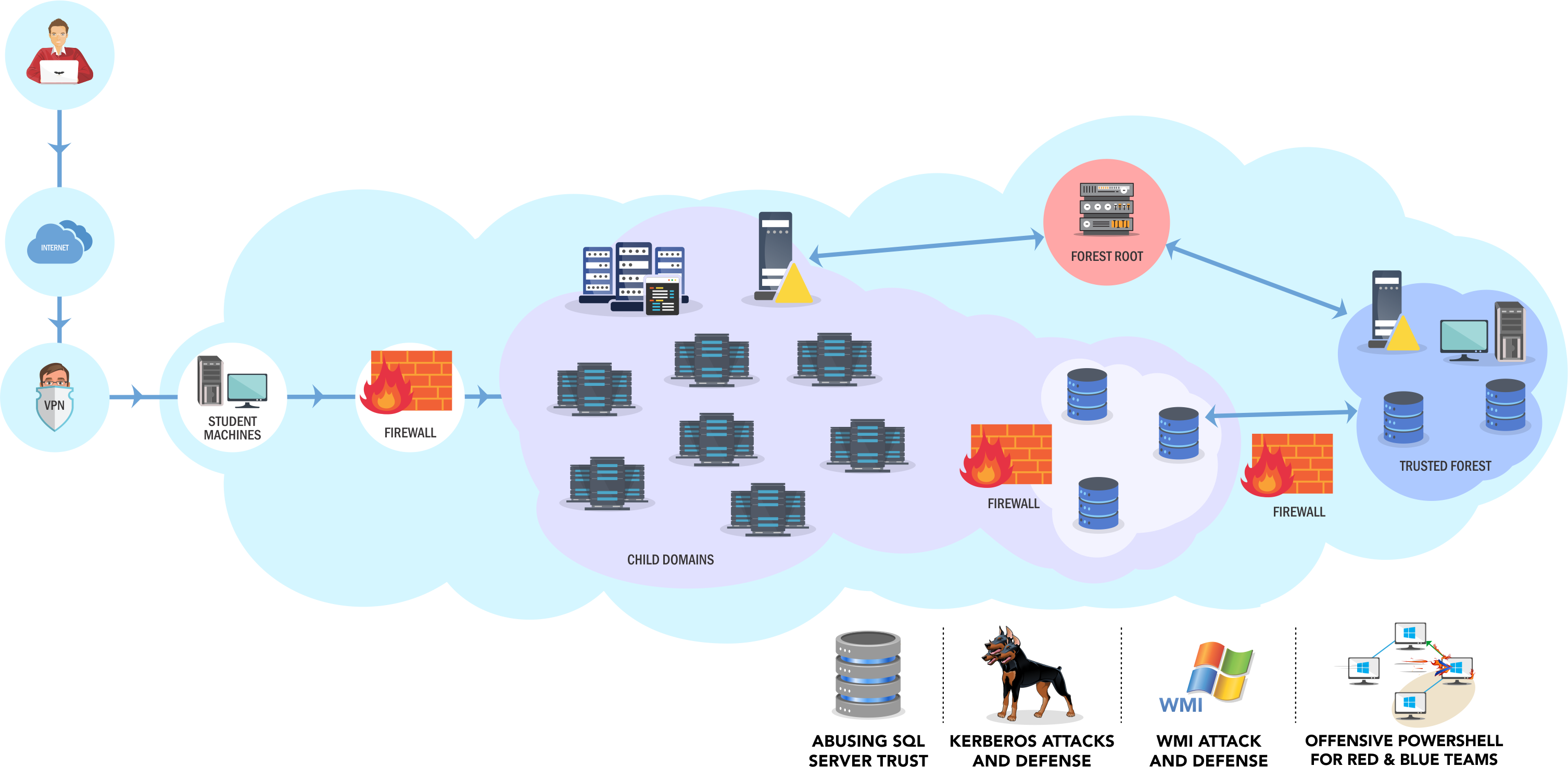 High level overview of the lab network
High level overview of the lab network
The lab and course
I bought access to 30 days of lab time. In addition to lab access, there PDFs and a few hours of videos taking you through some of the subjects you encounter in the lab. There are tons of learning objectives that follows a flag system to not only teach you enumeration, foothold and, but also a lot about the Windows file system, how credentials are stored, and occasionally how enterprise applications work in a Windows environment. Some of the subjects include the usual things like domain enumeration, escalation of privilege, but more specific and interesting subjects you might have not encountered before, like:
- MSSQL server and server links
- Attacks on and across domain and forest trusts
- Kerberos concepts
- Battling network segregation
- Phishing and payload generation
The lab is intended as a challenge, and the course does not cover everything you need to know. Having done the previous AD lab, I can tell you this is more challenging and requires you to do a lot of your own research. However, the lab team is very lenient with hints and provides good assistance if you ask nicely. Just a peek of some of the tools and frameworks I used in the labs:
Also, without spoiling the lab too much, I challenged myself to learn some more Powershell by writing a custom tool for a specific operation. It was a tool to password spray Jenkins instances. It can be found on my Github at chryzsh/Invoke-JenkinsPasswordSpray.
The exam
Since this is a certification, and not only a lab there is a 48 hour exam you have to pass to get the certification called Pentester Acadmey Red Team Expert. The pass criteria is not a strict x of out y amount of boxes, but is determined by Pentester Academy based on the quality of your report.
I will say that I did not find the exam as hard as the lab, but still had a good bunch of rabbit holes that forced me to think quite hard about what I was doing. I cleared the exam in good time, but it wasn’t without effort as I did spend nearly every waking hour of the 30 days I had in the lab hacking away, learning and retrying things.
It was very rewarding to completely compromise both the course and exam lab. I submitted a detailed report containing detailed description of identified vulnerabilities and recommendations for mitigating them. I also included a detailed writeup with screenshots of how I compromised the lab. Writing a professional pentest report is key to passing this exam.
Shortly after, I got a personal email from the big brain of it all, Nikhil Mittal thanking me once again for a good report and asking me for feedback. We traded some ideas about possible improvements, and I had the impression we agreed on most points. I hope other students can benefit from this.
Conclusion
Again, this was a very rewarding certification. The lab is challenging, thorough, and you won’t find anything that lets you learn Active Directory security as dynamically as this. Trust me when I say that Pentester Academy provides some of the best lab support that not only helps you with technical issues, but always pushes you in the right direction when you are struggling.
Once again, I can highly recommend this course for anyone looking to improve their skills in Active Directory security and penetration testing. And if you have any questions, please message me on Twitter or hit me up @crusher in the Bloodhound slack.
Other Active Directory labs
Many have asked me whether I can compare these AD labs to any of the other Active Directory labs available like those on Hackthebox. I still haven’t done all of those, but check the bottom section of my previous review for a list of labs I know of.

