Review of Pentester Academy - Global Central Bank (GCB)
You may have seen my previous reviews of the certifications Pentester Academy - Active Directory Lab and Pentester Academy - Windows Red Team Lab, which I did earlier this year. The first course is intended for Active Directory security beginners, while the second is more geared towards those wanting to learn more advanced Windows infrastructure concepts.
This is my review of Pentester Academy - Global Central Bank: An Enterprise Cyber Range which is the third in their progression of Active Directory oriented certifications, after the two I mentioned above. This course provides yet another an Active Directory lab that allows you to practice not only complicated attacks on enterprise infrastructure, but allows you to watch it with defensive eyes using a third party monitoring tool. This really shows you how loud you are, and you’re going to feel like you are staring at yourself in the mirror asking “am I always this ugly?”.
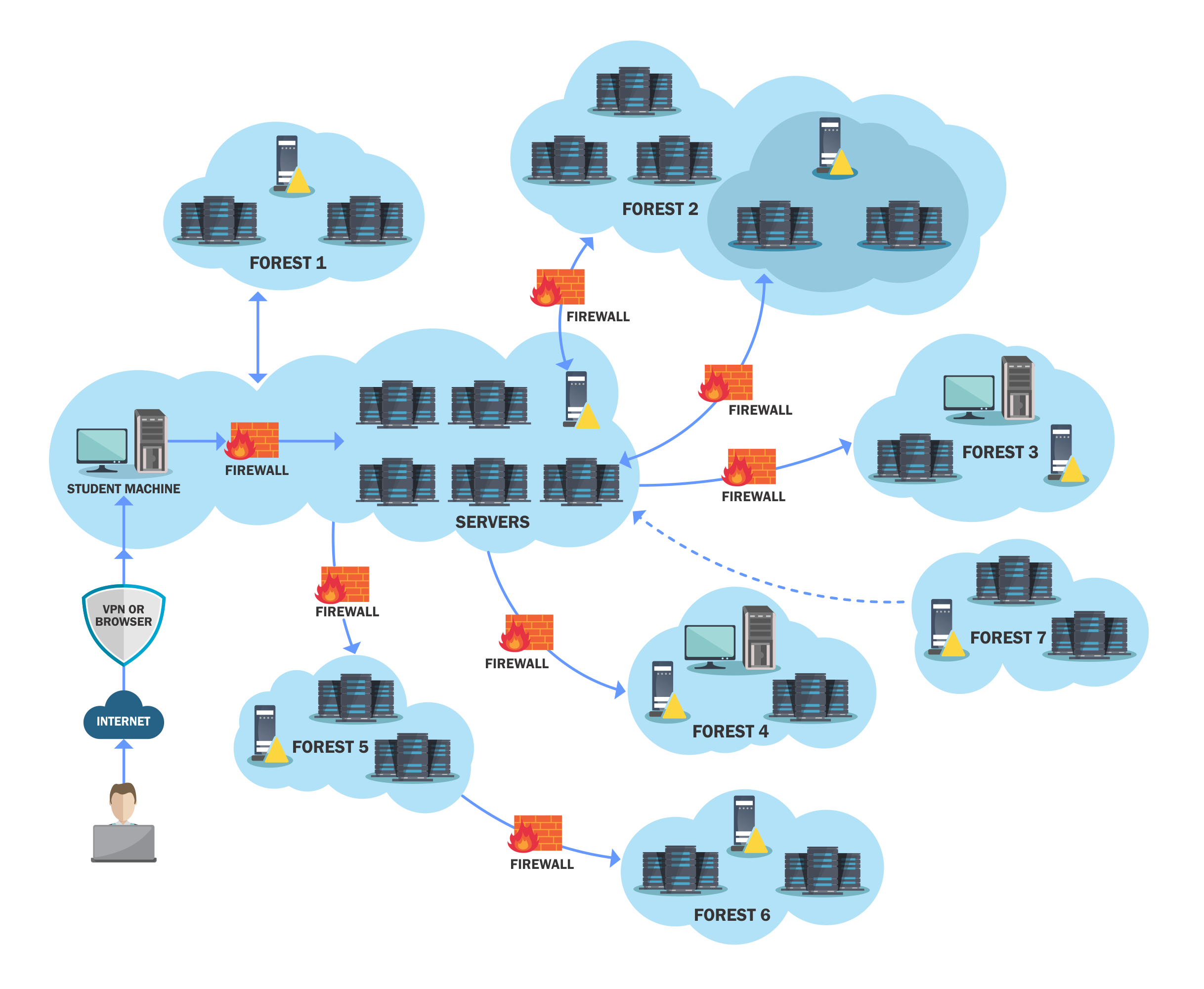 High level overview of the lab network
High level overview of the lab network
The lab and course
I’ve already written a lot about the previous courses so I will keep this short. The lab is very challenging. Even with a certain degree of experience this lab forces you into some very awkward edge-case style scenarios you most likely have never encountered. Without giving away too much, there were scenarios such as finding a single service running on hosts in a /16 behind a firewall, getting remote command execution on machines with application whitelisting and abusing ACLs across forests. I bought 60 days of lab time, and I just got through it, even when I pulled some full day 16 hour hacking sessions. So if you ask me, 60 days is the minimum should get, because it’s hard and you’re going to suffer a lot, just like I did.
Like the other courses, there was a course consisting of PDFs and videos covering the subjects. A lot of the concepts were new to me, and it was very cool to try some of the attacks and Active Directory features first hand. Here are some of the concepts covered:
- PAM trusts
- LAPS
- “The printer bug”
- Resource based constrained delegation (which I did a blog post on earlier)
- Exchange permissions
- Just Enough Administration
The exam
Like the previous red team lab, this certifications sports a 48 hour exam. The main difference from the two previous exams was a bit of a different structure. This exam has an attack and a defense part, where the two parts are weighted 50/50. This means that after you hack your way through to Enterprise Admin you have to mitigate as many vulnerabilities as you can. I thought this gave the exam a very cool edge that I haven’t seen anywhere else. I did however feel like the course and lab did not prepare me as well for the defense part as it did for the attack part. But who said the exam was going to be easy?
Like the other two certifications, a proper pentest report is required to pass. It must include detailed writeups of the attack and mitigation of vulnerabilities in the lab environment. I did so to the best of my abilities, and even though I realized I had missed a few things the same night I had sent my report, I was fairly confident I would pass.
I woke up two days later to one of the most relieving emails of my career:
Congratulations! You have cleared the examination! You are now a PentesterAcademy Certified Enterprise Security Specialist.
Once again, Nikhil Mittal reached out and we once again discussed some potential improvements for the lab and exam. I think this is a very nice touch to the whole certification experience, especially for platforms like this, which aren’t always as polished as you might expect.
Conclusion
Again, this is probably the hardest certification I have done so far in my career. But it was like the two previous ones, intensely rewarding to get it. I’m also proud to share that I am the first individual to acquire the PACES certification.
I think this is probably the most up-to-date Active Directory security certification you can get, and I can absolutely recommend it to anyone who is up for a grueling, but rewarding challenge. If you have any questions, please message me on Twitter or hit me up @crusher in the Bloodhound slack.

